To get reliable data and logs of an AutoPilot and/or PPD (aka WhiteGlove) enrollment, I wrote a few simple scripts.
A set of these scripts is used for the LOCAL capture of the data on a freshly rolled box, whether successful (green screen) or faulty (red screen).
Another requires read access to the tenant (MEM, Intune) and provides two very meaningful CSV files to the devices and to the events in the Intune, which can be easily dealt with with Excel.
The scripts are based on the „built-in“ mdmdiagnosticstool.exe and the WindowsAutoPilotIntune PowerShell module by Michael Niehaus as well as the Microsoft.Graph.Intune PowerShell Modul.
Titbit:
When a USB stick is connected (recommendation) and you start the parts from there, the parts write their data to a directory on the stick (with the serial number of the box in the name on which they are executed).
Otherwise, they write to %temp% of the respective user who runs them.
Local data capture
Recommendation: DO record the QR code (there are numerous apps 😊 for this task)
Press „Shift“ F10, then a CMD prompt should start.
Inside that cmd prompt (e.g. from the USB stick) run the script get-local-autopilot-infos.cmd, which internally calls the MdmDiagnosticsTool.exe and then starts another PowerShell script (Get-AutopilotDiagnostics.ps1) by Michael Niehaus).
The latter can be installed as follows or copied from a box where it was already installed (I did this here & packed it into the gleiuchen folder where the calling CMD is located 😊 )
Install Script Name Get-AutopilotDiagnostics
Source:
PowerShell Gallery | Get AutopilotDiagnostics 5.6
Of course, the whole thing also works WITHOUT a PPD / WhiteGlove sequence 😊
PowerShell Modul Microsoft.Graph.Intune
Install-Module Microsoft.Graph.Intune -Force
Source:
PowerShell Gallery | Microsoft.Graph.Intune 6.1907.1.0
On a box that has already been completely enrolled, however, you need admin rights for the execution of the scripts, which is given in the OOBE phase (see above) 😊
Further Titbit:
The get-local-autopilot-infos.ps1 also does the following:
copy json files
$CMD 1 = „copy C:“Windows“ServiceState“wmansvc“„ “ + $OutAPDir
So it also copies the JSON files created during the enrollment into the output dir, was a real „secret tip“ of Mike, also these files are quite meaningful 😊
Furthermore, some relevant EVTX files are generated, which the mdmdiagnostics.exe tool does not capture or does it only unstable ( ☹ ).
And all IME (Intune Management Engine) logs are copied too 😊
Finally some relevant REG Keys (HKLM) get exported & copied too.
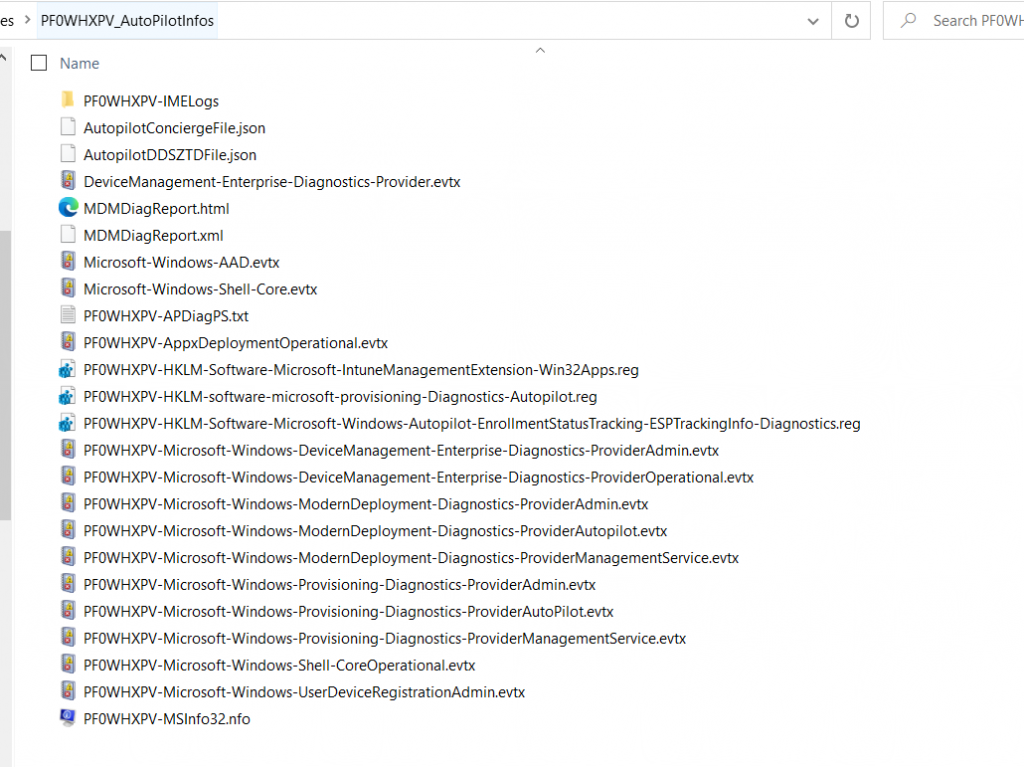
And a further tibit:
If you want to have all the XMLs and JSONs really readable & also want to take apart and if necessary edit, take / woman the following tool, what I re-discovered recently:
The JSON Buddy
This tool is able to migrate XML 2 JSON vice versa 😊
And it has an excellent and comprehensive GUI 😊
Collection of tenant data (online)
This requires access to the respective tenant and at least the PowerShell module WindowsAutoPilotIntune (by Mike)
The same can be installed as follows:
Install Modules Name WindowsAutoPilotIntune
Source:
PowerShell Gallery | WindowsAutoPilotIntune 4.8
The part outputs at the end where it has placed the CSVs, as I said preferably again on a USB stick, otherwise stop in the %temp% of the calling user, e.g.:
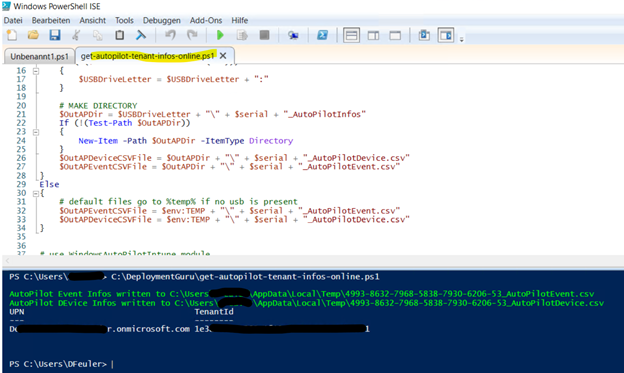
Helpful links to analyze the data
Mike & Anoop have already described in their blogs in many details how to „take apart“ the resulting data 😊
Recommendation here:
the EVTX from the „Shell-Core“ is COOL 😊
Windows Autopilot diagnostics: Digging deeper – Out of Office Hours (oofhours.com)
Troubleshooting Windows device enrollment problems in Microsoft Intune – Intune | Microsoft Docs
MDM Diagnostics Tool – Autopilot Troubleshooting 5 Easy Tips (anoopcnair.com)
The scripts for the local capturing are here
The script for the online capturing is here
HAPPY DEBUGGING 🙂
